If you have any questions, you are always welcome to contact us. We'll get back to you as soon as possible, within 24 hours on weekdays.
-
Shipping Information
Use this text to answer questions in as much detail as possible for your customers.
-
Customer Support
Use this text to answer questions in as much detail as possible for your customers.
-
FAQ’s
Use this text to answer questions in as much detail as possible for your customers.
-
Contact Us
Use this text to answer questions in as much detail as possible for your customers.


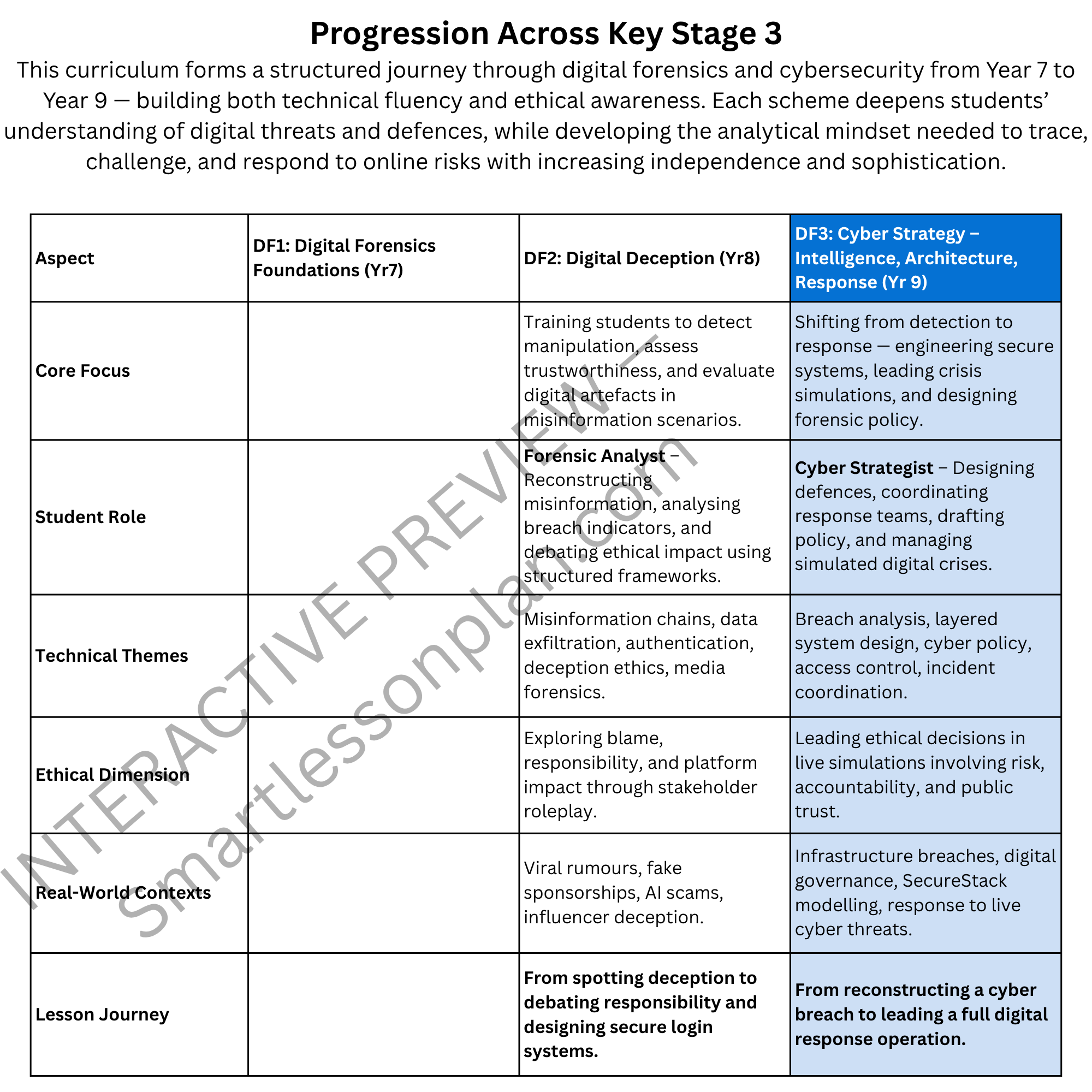

DF3 Scheme of work: Cyber Strategy Intelligence, Architecture, Response.Year 9 (6 Lessons)
Teach cybersecurity like it actually works
A complete 6-lesson KS3 Computer Science scheme exploring digital forensics, secure system architecture, and real-time incident response - with no coding, no extra tools, and everything ready to teach.
Perfect for:
-
Non-specialist teachers
-
Curriculum and subject leaders
-
High-ability Year 9 classes and fully supported for mixed-ability teaching
-
Inspection-focused departments
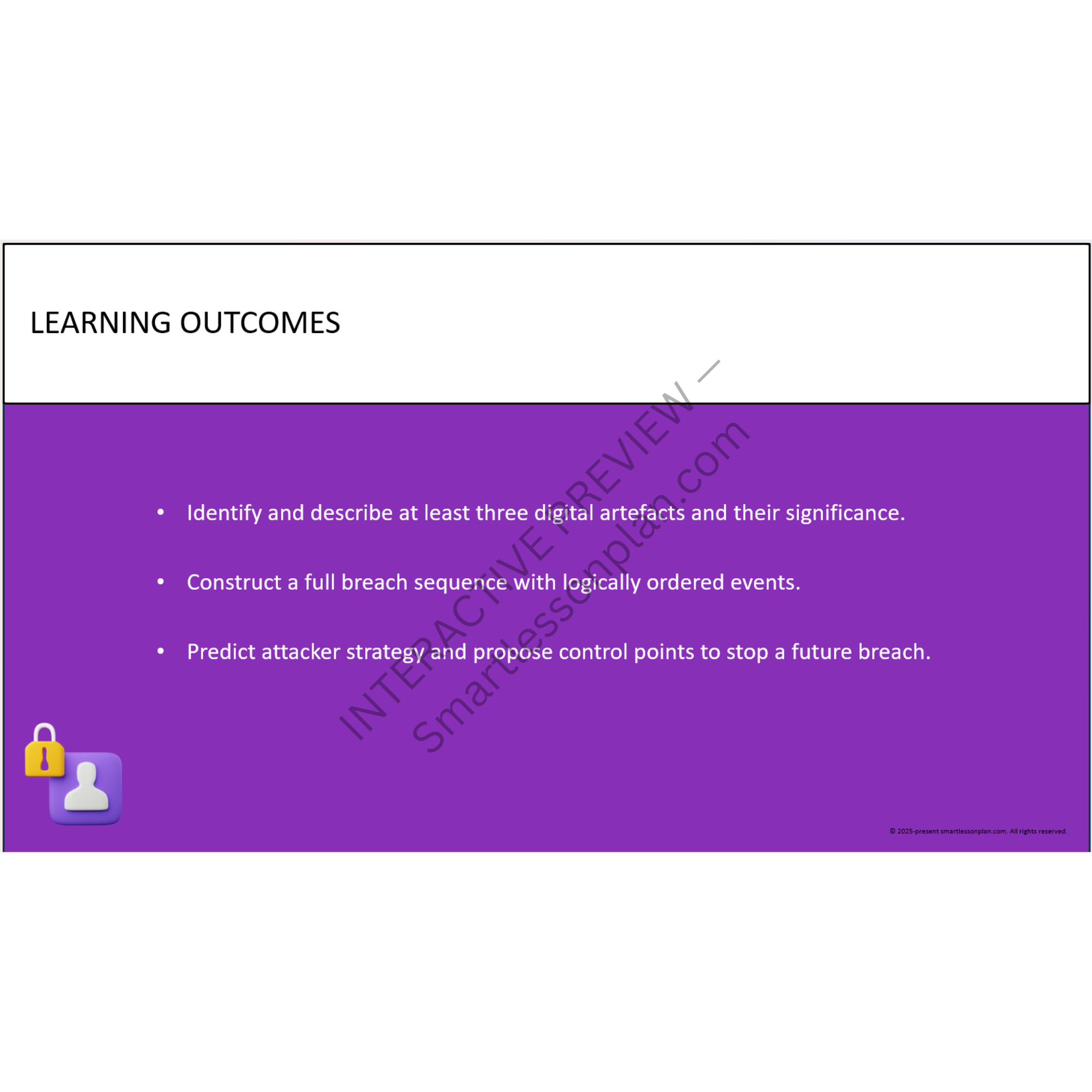
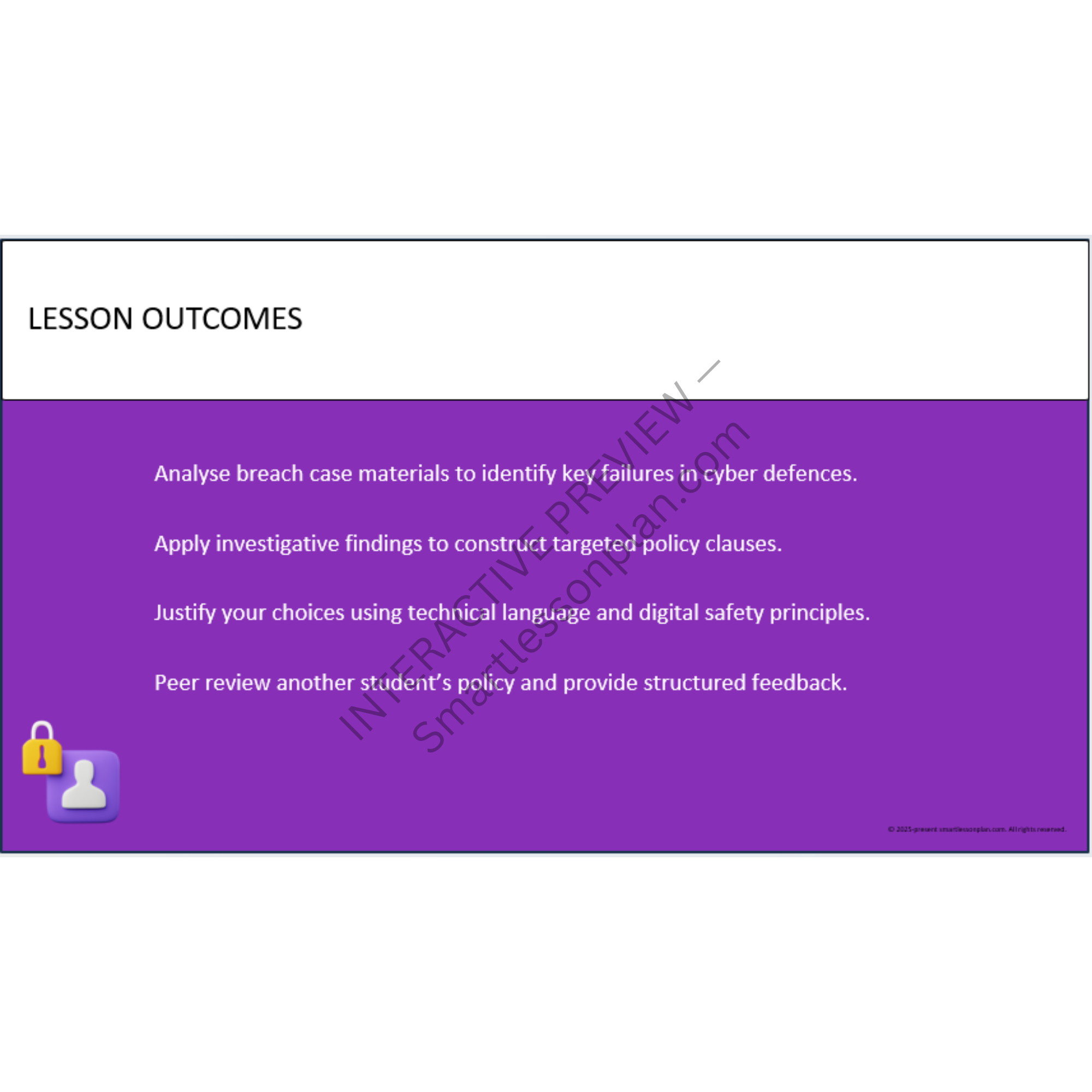
What students learn
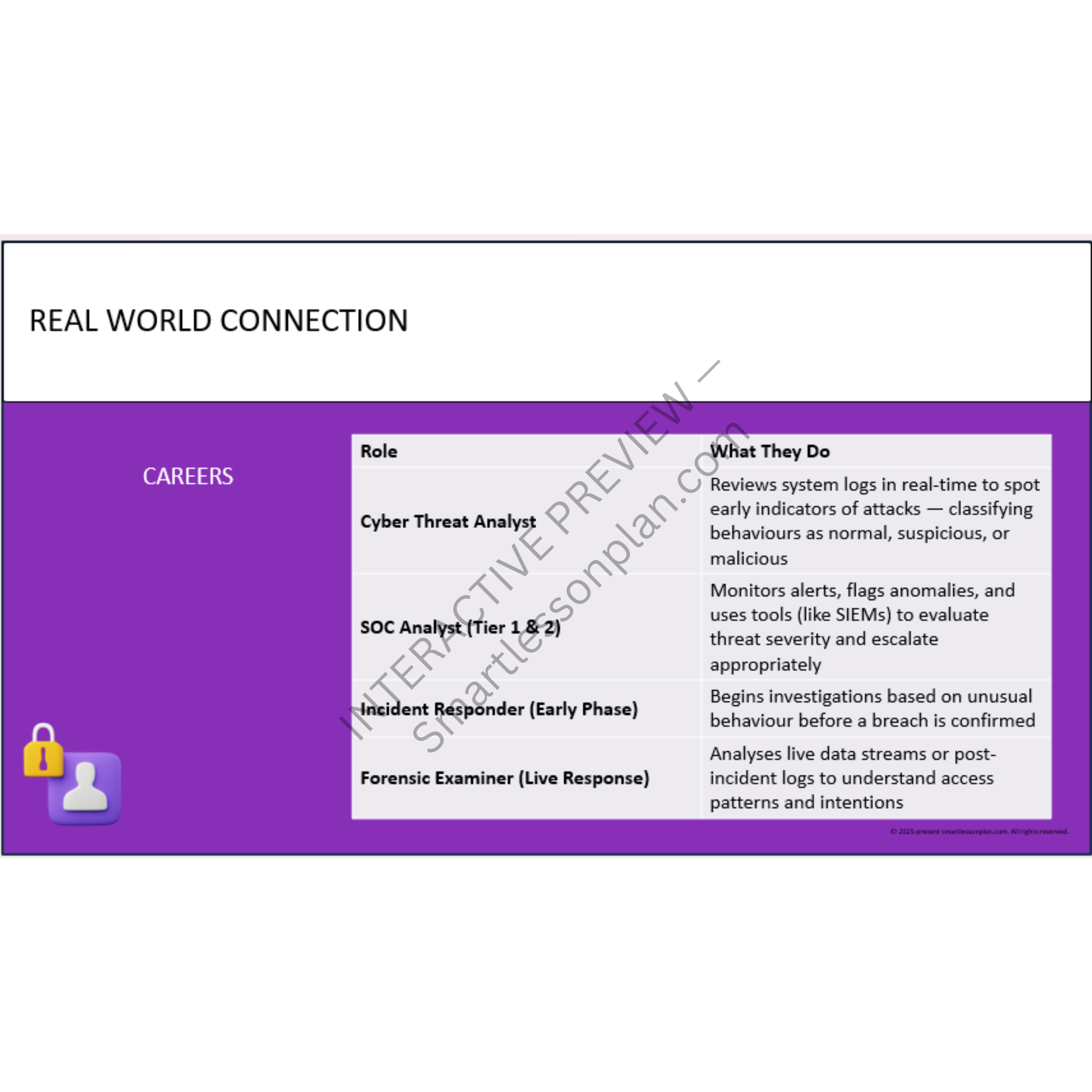
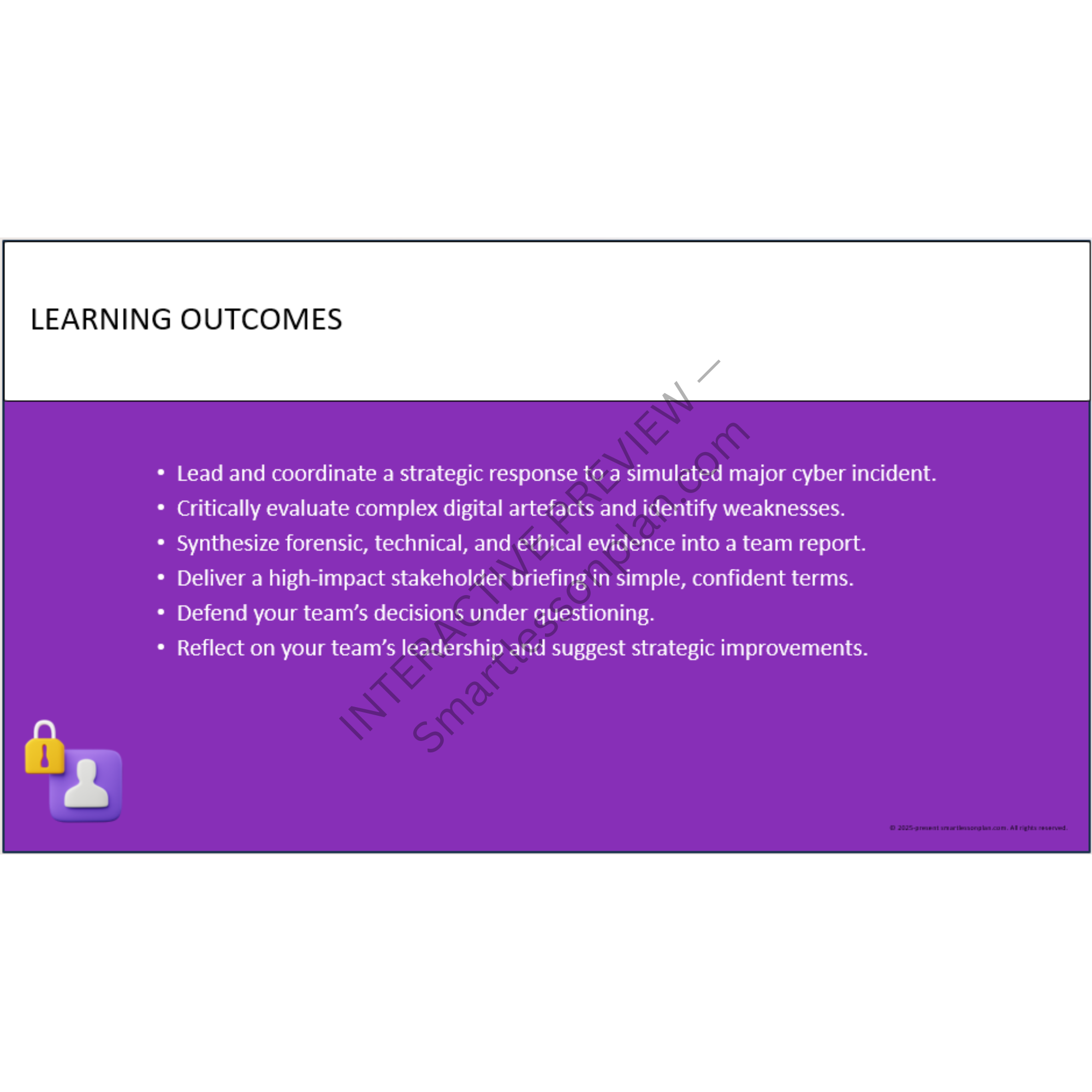
DF3 trains students to think like real cybersecurity professionals - analysing breaches, designing layered systems, and leading team-based responses in live simulations.
Each lesson mirrors the real roles found in cyber operations centres, guiding learners from digital investigation to strategic response - all using offline, printable, classroom-safe resources.
🔹 Students don’t just learn about cybersecurity - they reconstruct it, simulate it, and justify it.
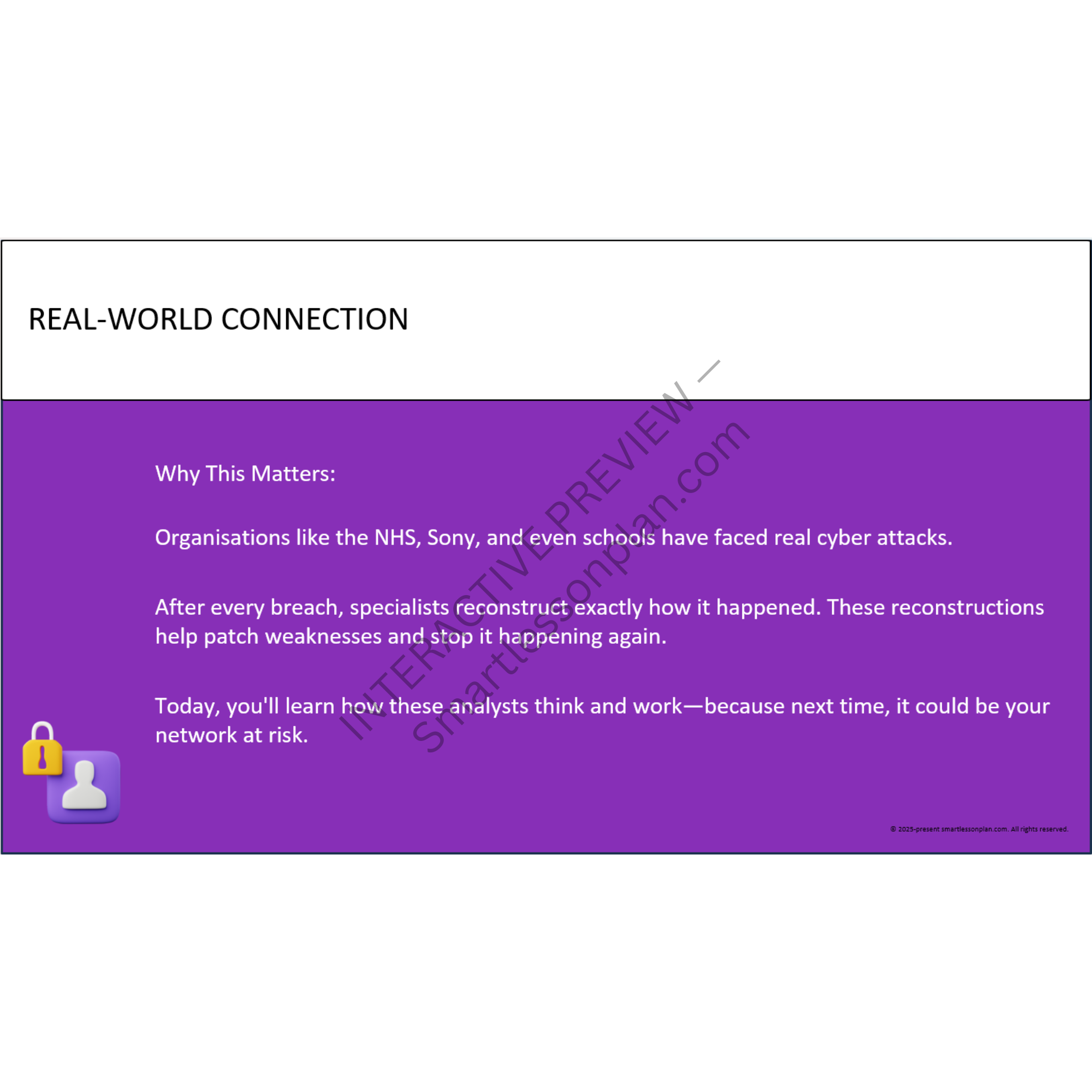
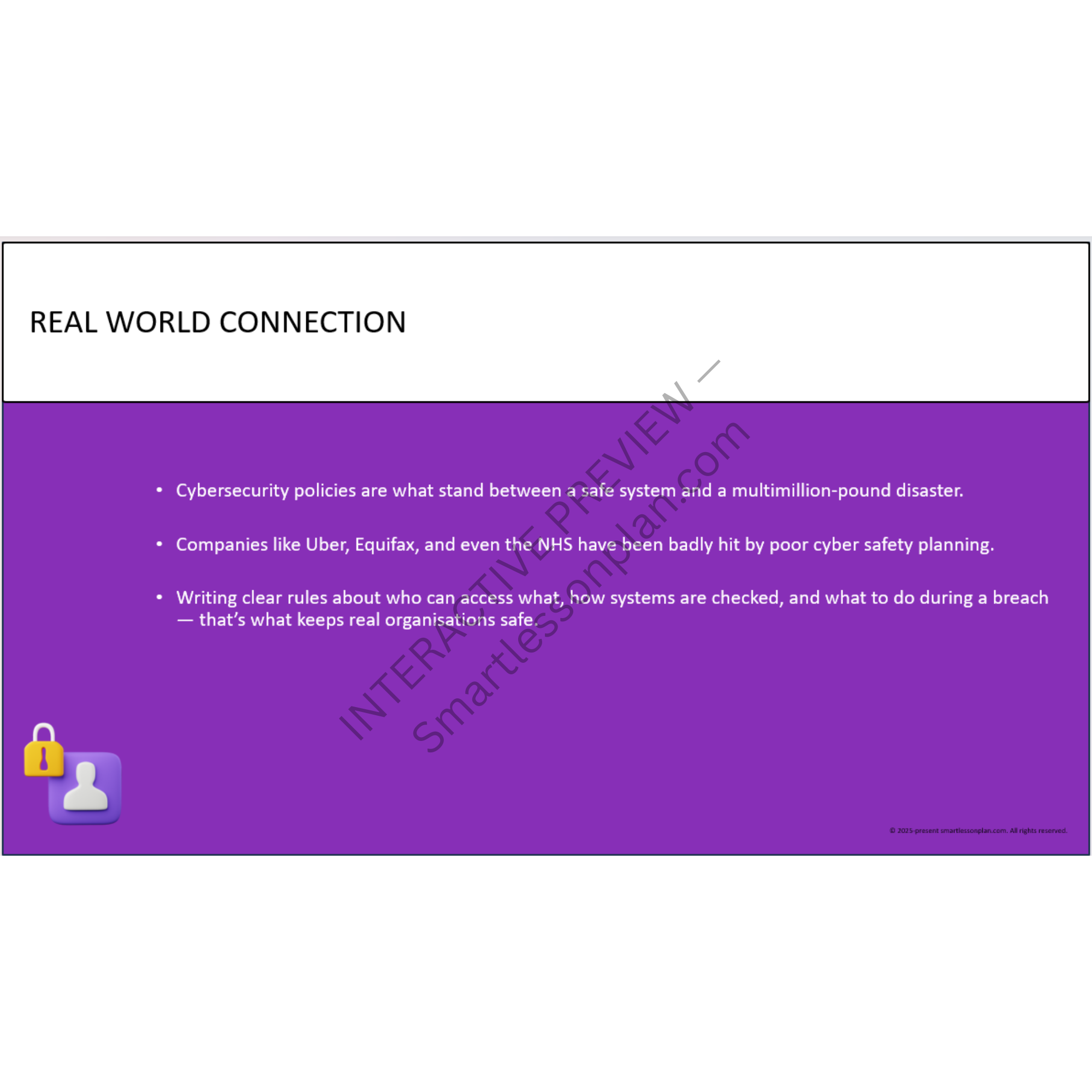
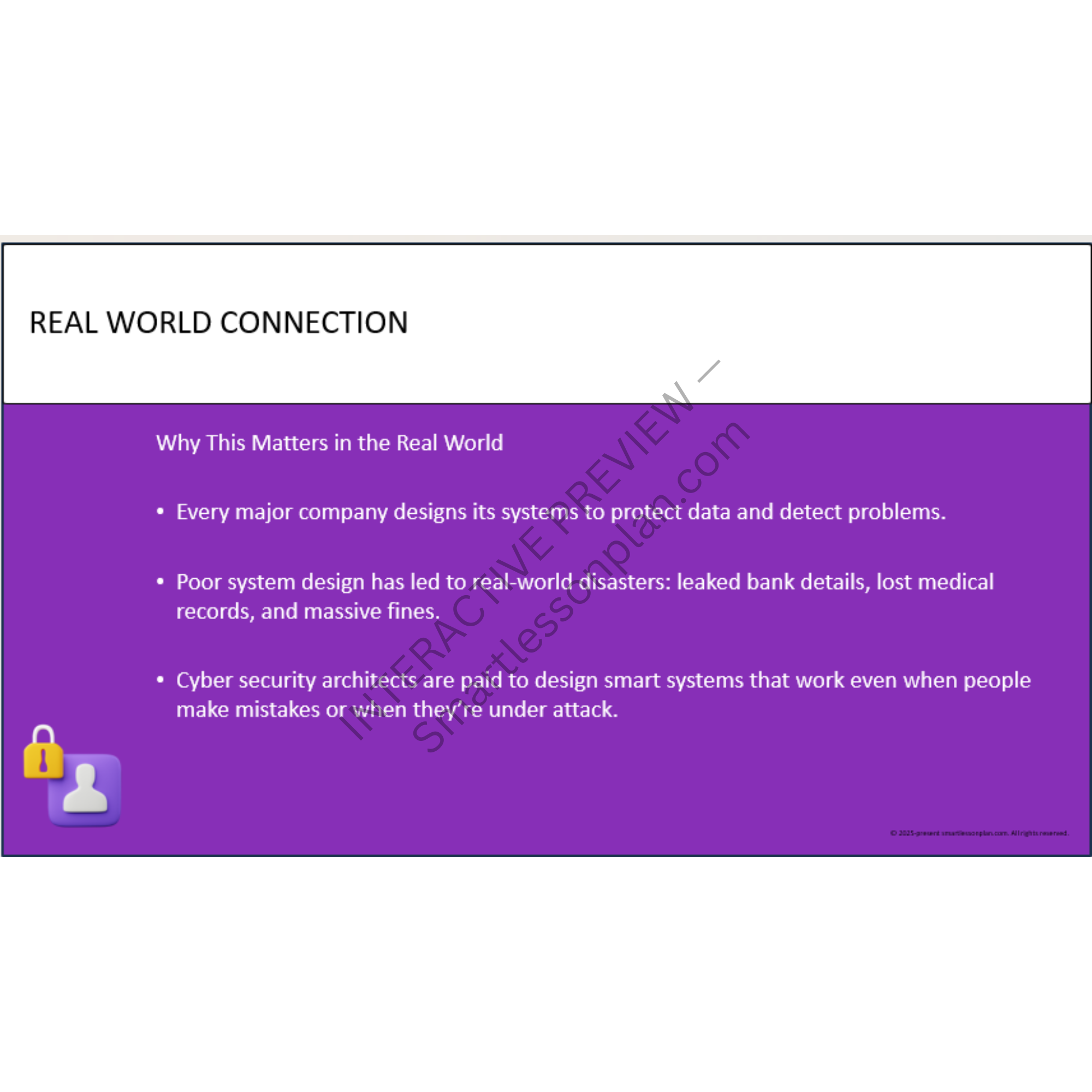
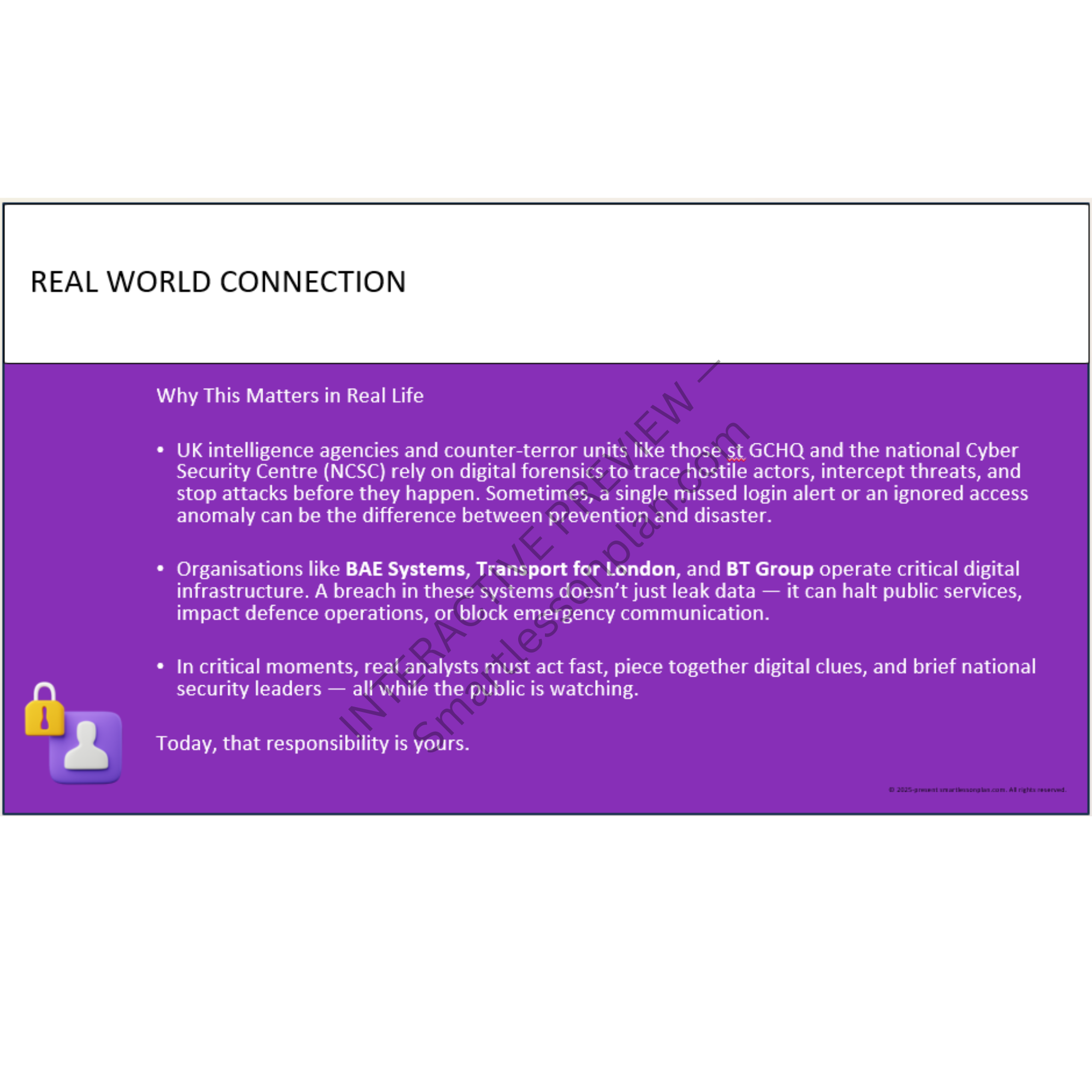
Why go beyond cyber awareness?
Most students know how to stay safe online.
But very few can explain how systems work, how they fail - or how to recover them under pressure.
This scheme fixes that.
Through hands-on forensic artefacts, decision-based modelling, and secure design challenges, students explore how digital systems are protected - and what happens when they’re not.
Lesson structure & progression
Each session builds step-by-step across three real-world cyber disciplines: investigation, architecture, and response.
Lesson titles and focus:
-
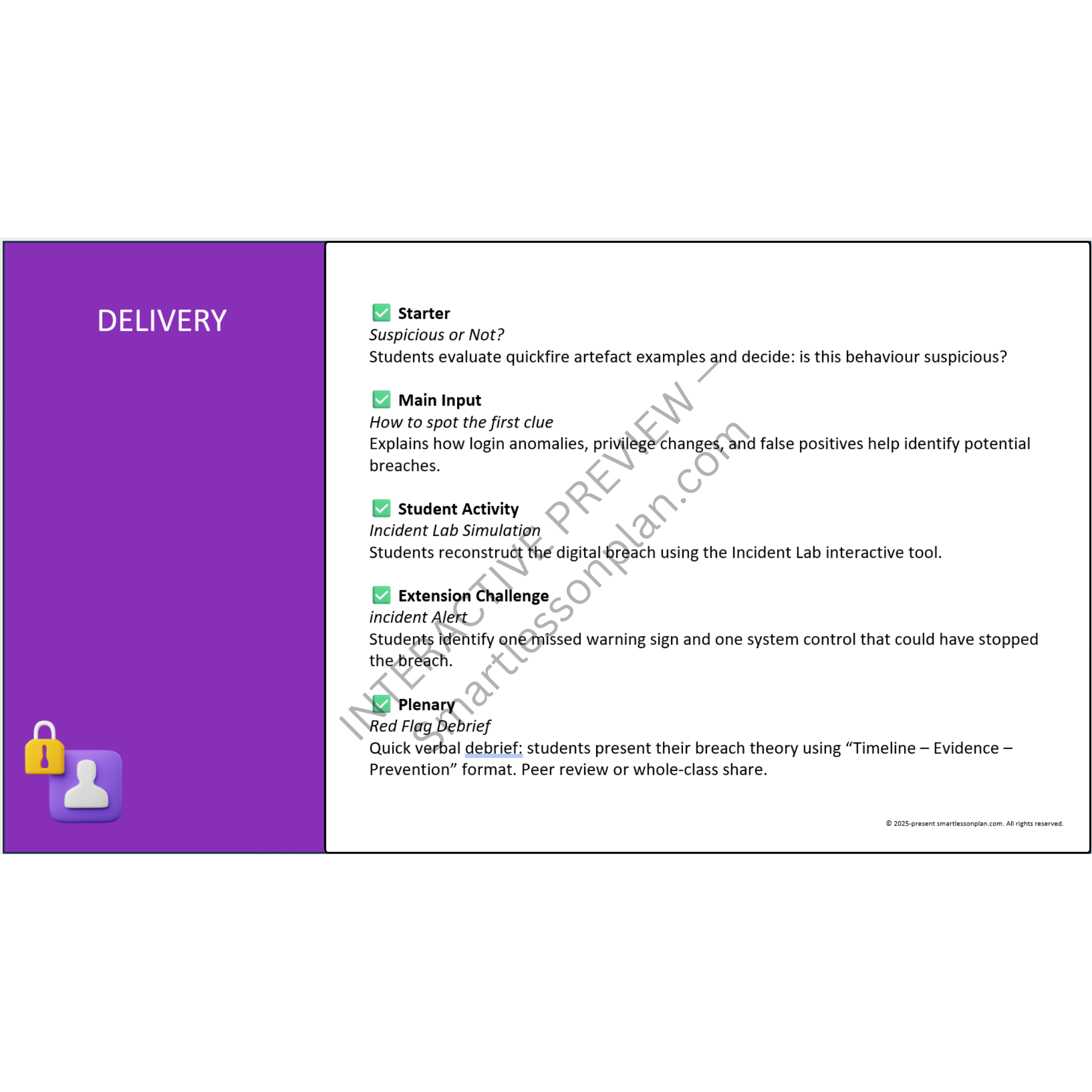
Reconstructing a Live Cyber Attack
Investigate a breach using timestamped artefacts. Build a timeline to explain what went wrong - and why. -
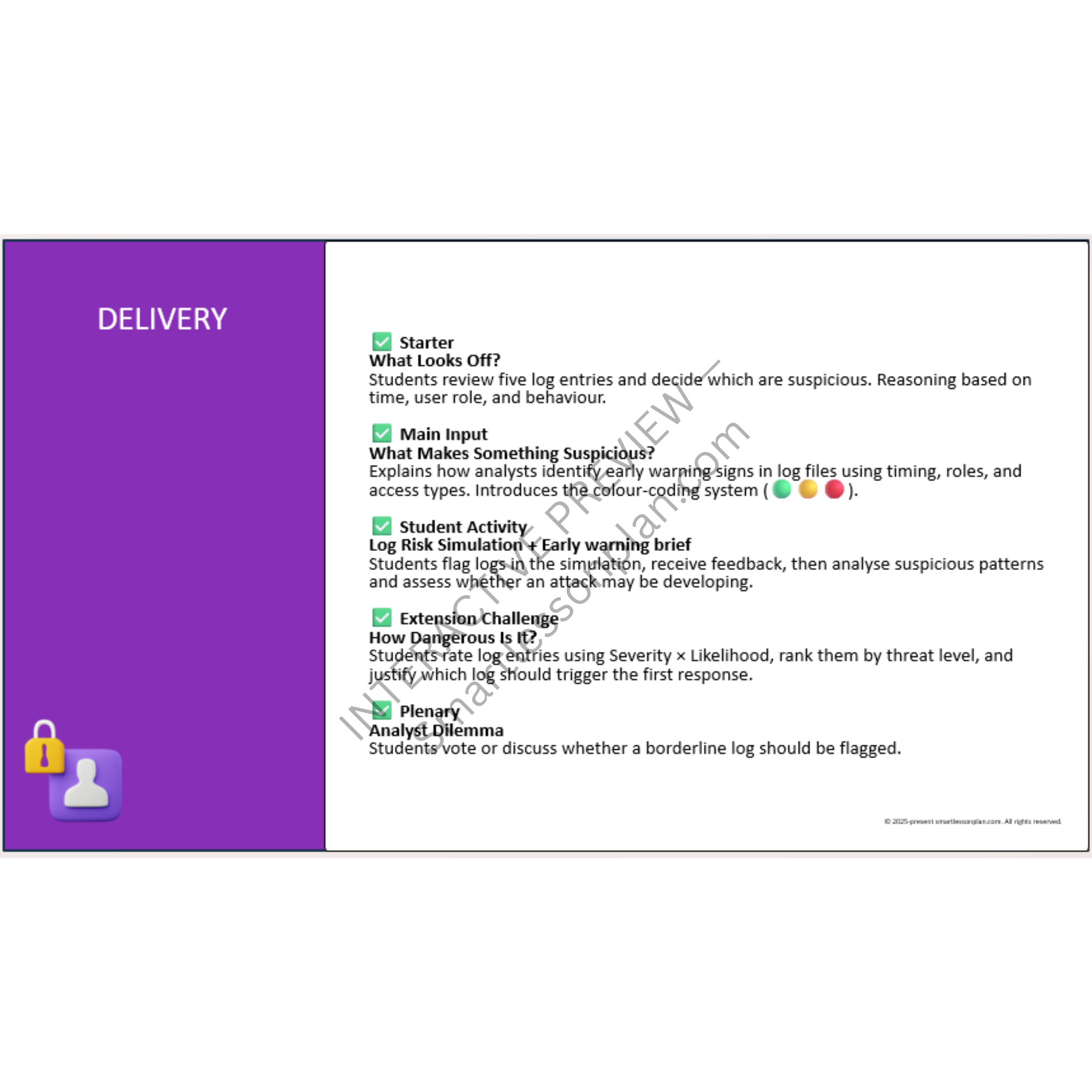
Early-Stage Cyber Defence
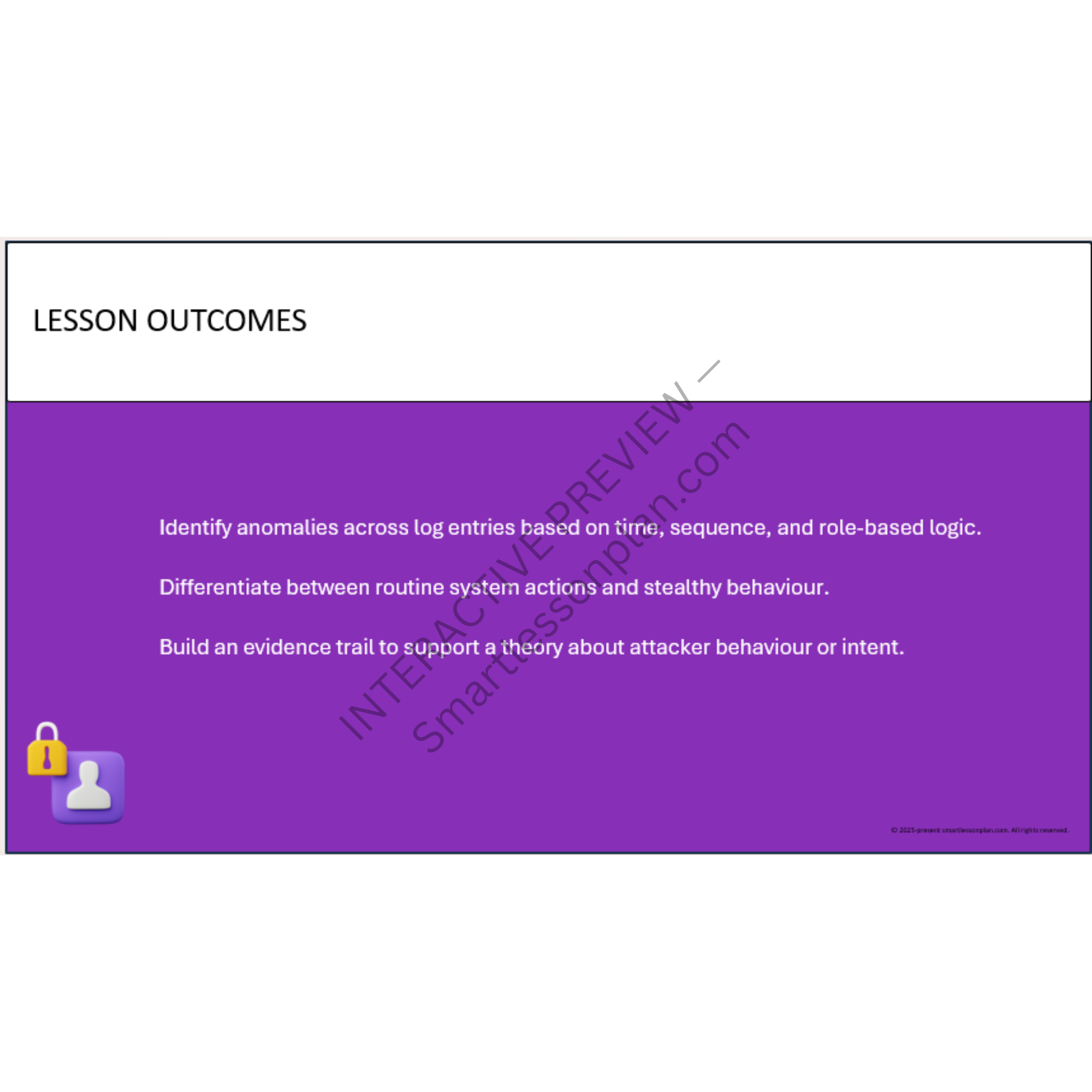
Classify suspicious behaviour in log files using a risk matrix and anomaly detection simulator. -
Designing Smarter Cyber Defences
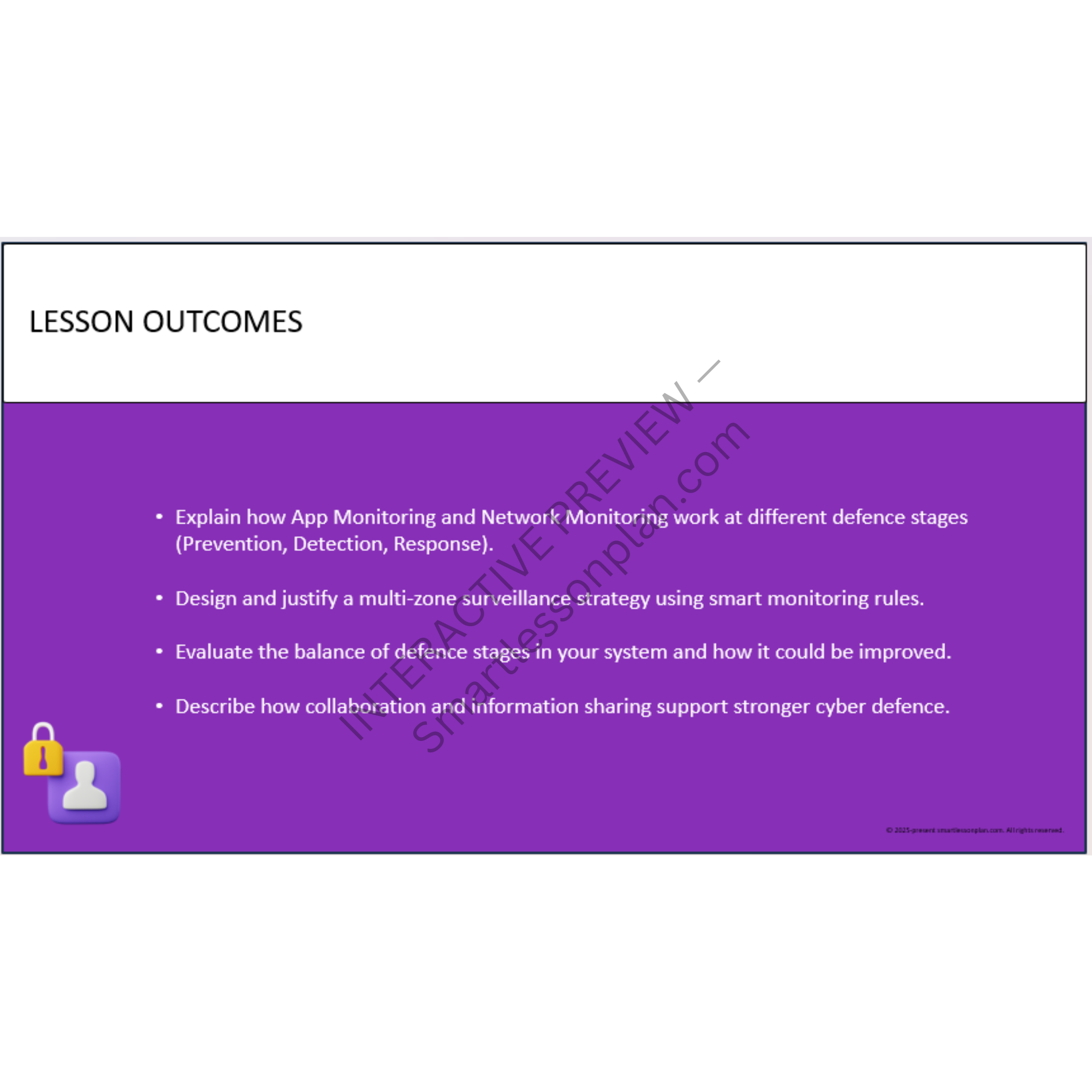
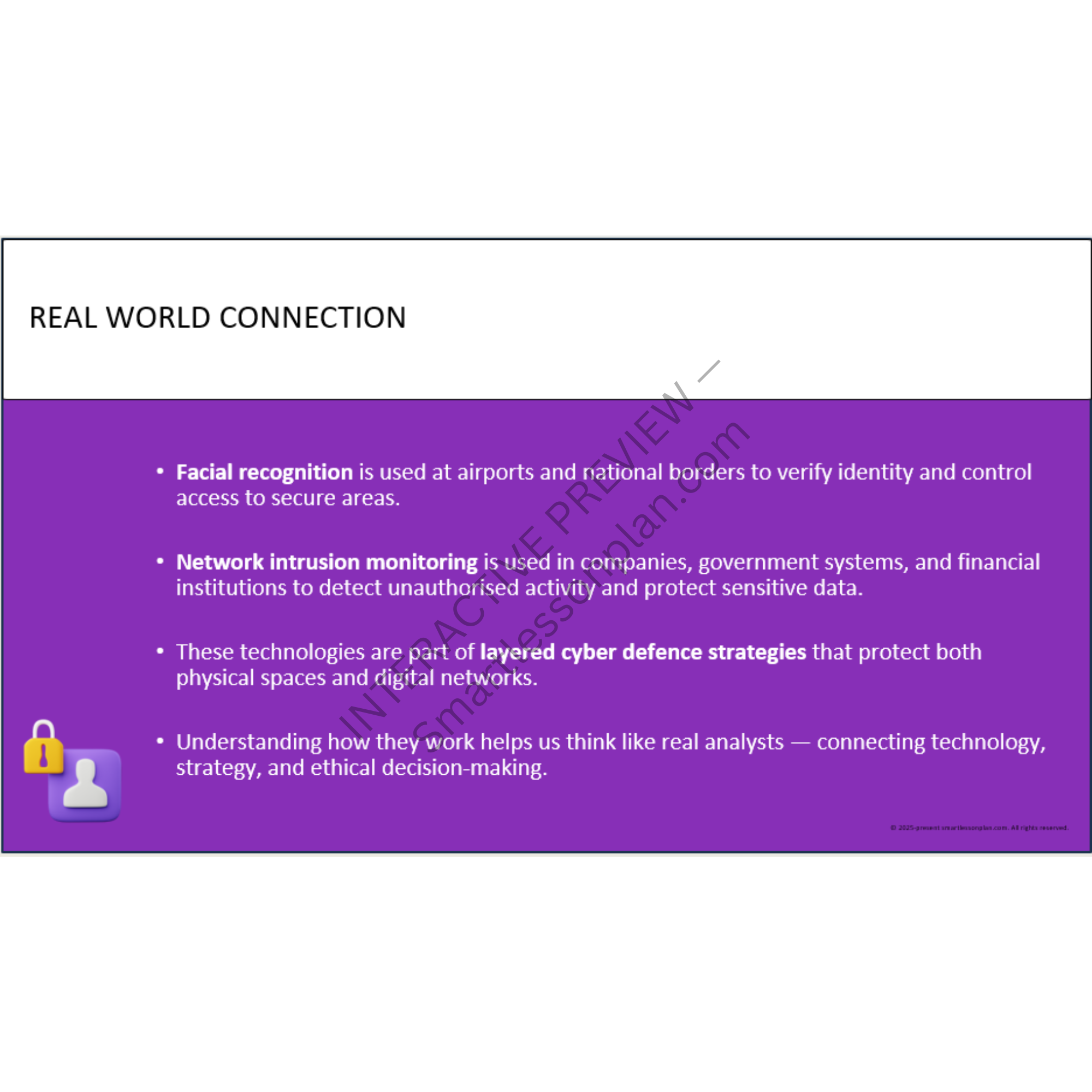
Explore real surveillance tools (App Monitoring, Network Monitoring) and how they're used to prevent, detect, and contain threats. -
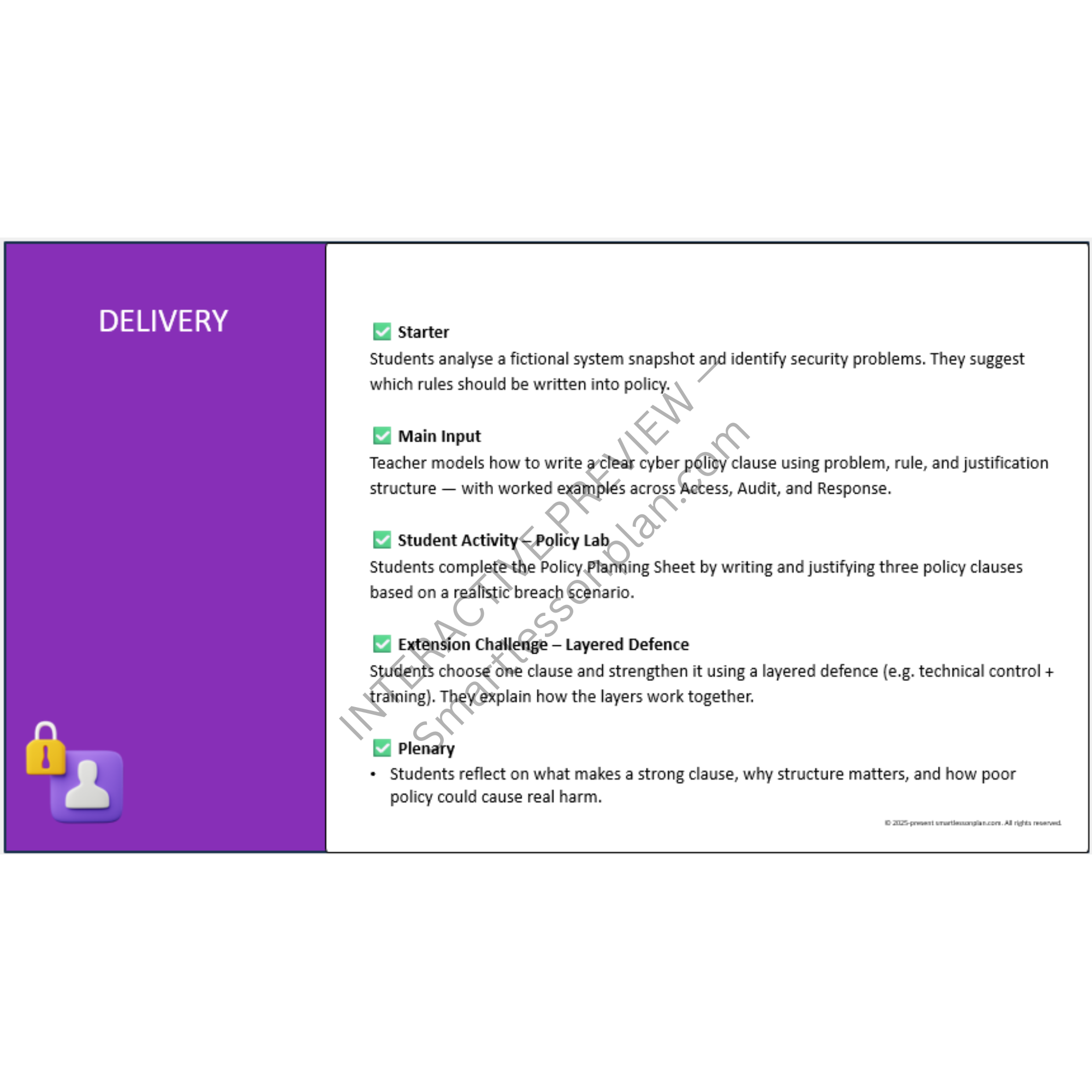
Policy Lab - Cyber Governance in Action
Draft structured policy clauses from forensic evidence, including access control and incident handling. -
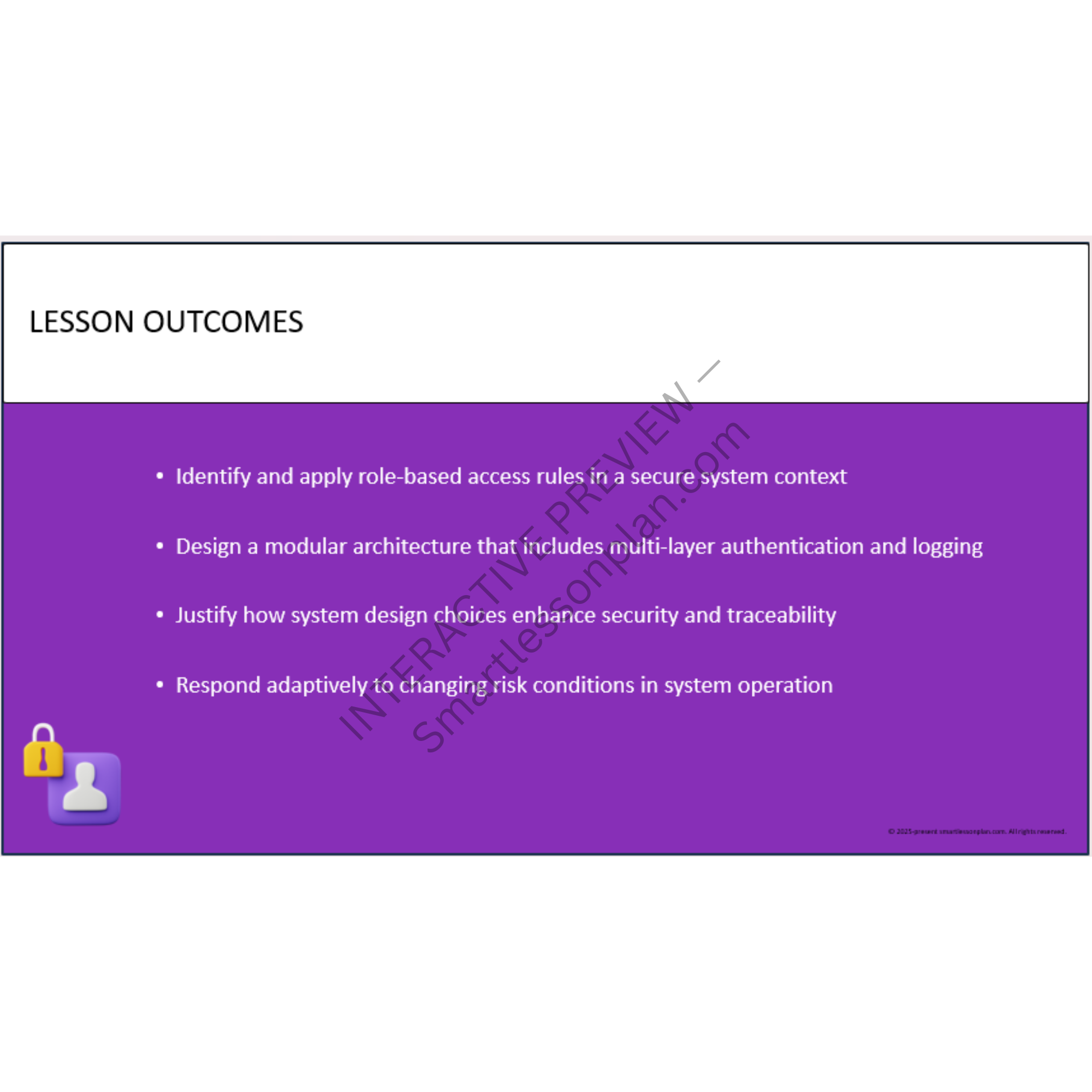
Designing a Secure System Architecture
Use the Secure Stack model to build a traceable, layered digital system with embedded triggers and access restrictions. -
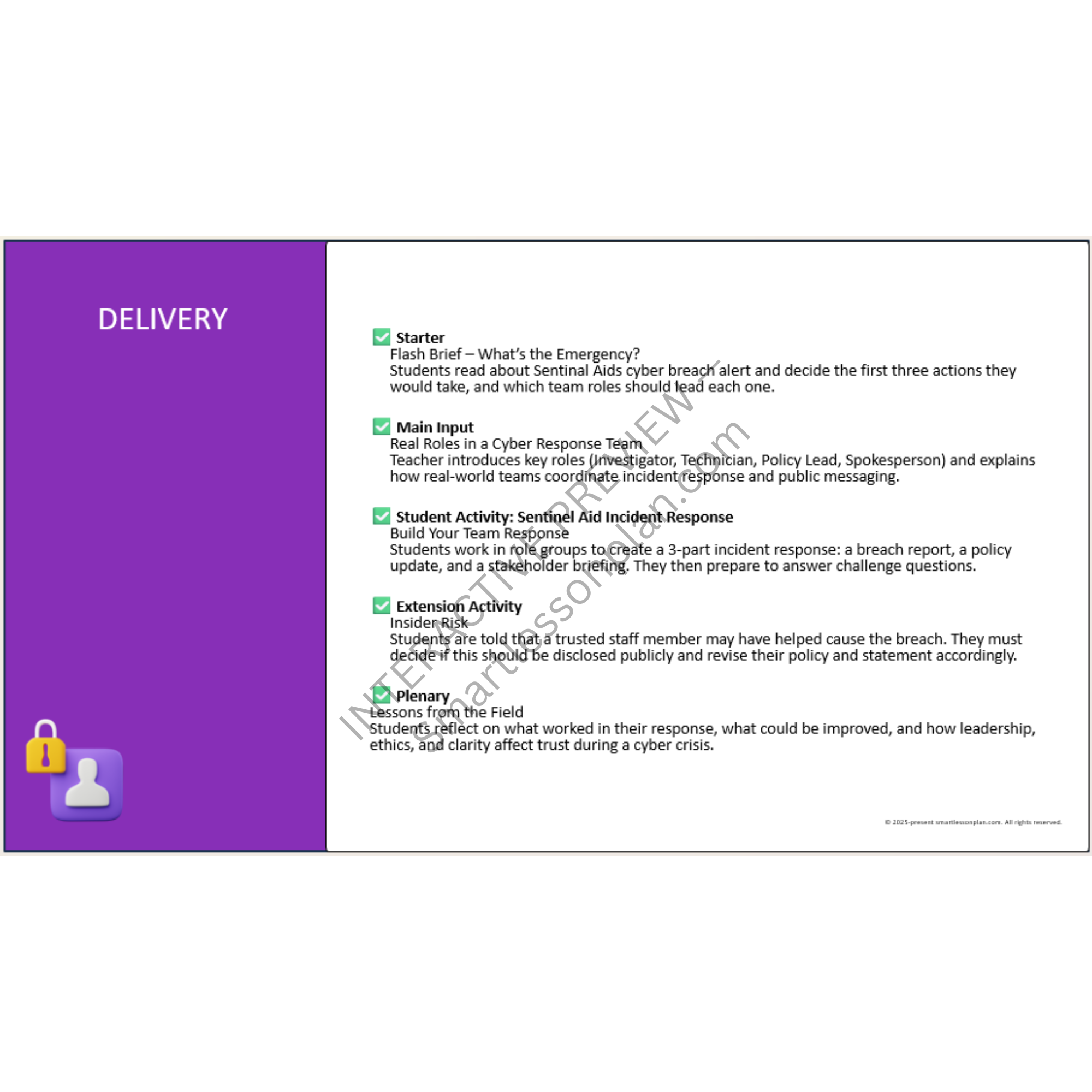
Coordinating a Cybersecurity Incident Response Team
Lead a live response simulation, assign analyst roles, brief stakeholders, and defend your decisions under challenge.
What you get
Everything is fully resourced, printable, and designed for confident classroom delivery:
- 6 structured, inspection-ready lesson plans
- PowerPoints with fully scripted speaker notes
- Offline simulations - no coding, no software
- Printable student activities with model answers
- Key vocabulary banks and editable templates
- SEND scaffolds and full classroom adaptation guides
- Optional cover lesson format for any session
- Full Scheme Inspection Report (intent, implementation, impact)
Built-in for inspection – without the extra workload
Every DF3 scheme includes a full inspection readiness report:
-
Curriculum Intent – Clear sequencing, ambition, accessibility, and real-world relevance
-
Implementation – Delivery model, resource structure, and differentiation
-
Impact – Evidence of progress, reasoning, and applied understanding
-
Inclusion & Accessibility – SEND scaffolds, cultural capital, and classroom equity
Subject leaders get everything they need to present high-quality computing provision - clearly and confidently.
Why this scheme works
Real-world relevance
Students simulate forensic investigations, build secure systems, and lead incident teams - just like real cybersecurity roles.
Teacher-friendly delivery
Everything is printable, scripted, and step-by-step. No specialist knowledge or technical setup required.
Inspection-proof
Fully documented outcomes, structured planning, SEND support, and measurable student progress.
Future-ready skills
Builds technical reasoning, digital confidence, and system-level understanding - preparing students to protect the digital systems of tomorrow.
Pairs well with
A next-gen lesson that keeps your curriculum aligned with emerging trends in computer science
Built for formal scrutiny - structured around intent, implementation, and impact
Schemes includes a full inspection report
Packed with high-standard classroom activities for high ability as well as mixed ability teaching
Includes full slide-by-slide speaker notes to support confident and consistent delivery
Keeps your curriculum sharp and future-facing - with topics that reflect today’s most relevant computing advances

DF3 Scheme of work: Cyber Strategy Intelligence, Architecture, Response.Year 9 (6 Lessons)