

DF3: Lesson 1: Reconstructing a Live Cyber Attack
Could your system catch a hacker before it’s too late?
Launch your digital forensics unit with a real-world breach investigation students won’t forget.
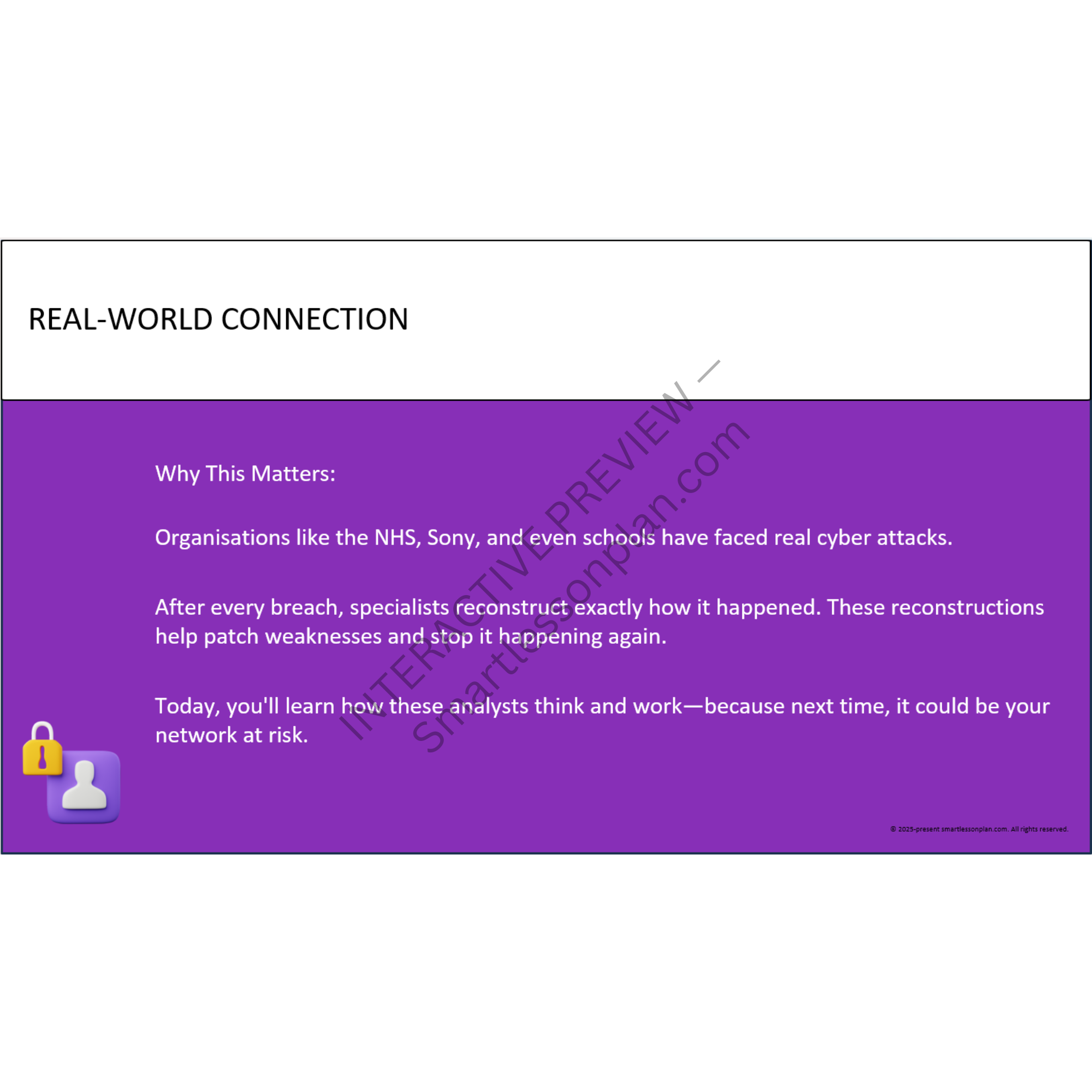
This KS3 / lower secondary computing lesson kicks off the “Cyber Strategy: Intelligence, Architecture, Response” scheme with an immersive offline simulation of a live cyber attack. Students step into the role of security analysts investigating a breach at an elite Olympic data centre.
They examine authentic-style artefacts - including login traces, system alerts, and user behaviour logs - to reconstruct the attack timeline, spot where the system failed, and propose realistic defences.
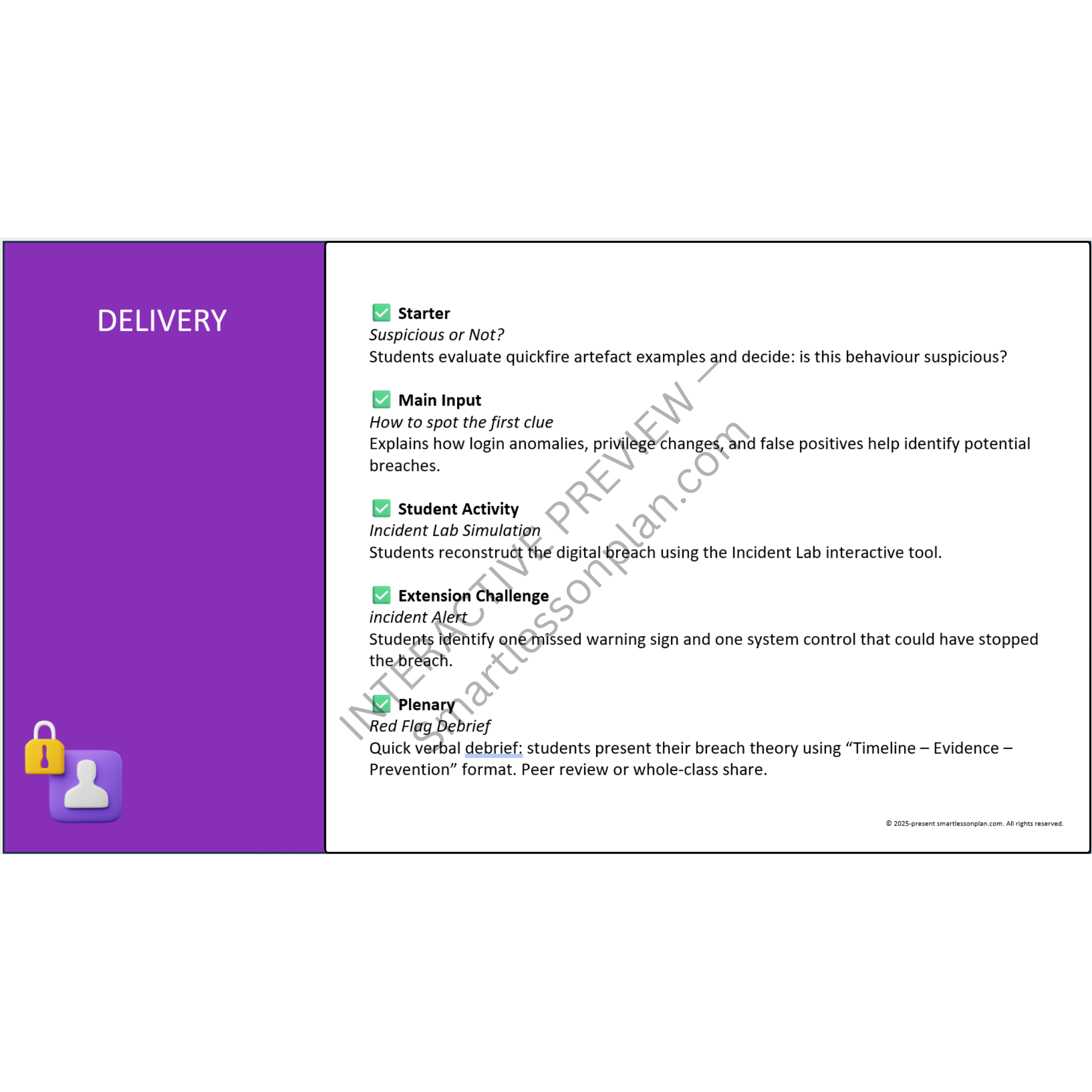
The lesson combines professional forensic logic with classroom-ready support, including a guided timeline simulator, structured analyst report, and optional strategic extension challenge. Activities build rigour step by step, with students producing a full breach reconstruction and delivering a 90-second incident debrief using evidence-based reasoning.
It’s hands-on, high-impact learning that connects cybersecurity principles to the real decisions that protect modern systems.
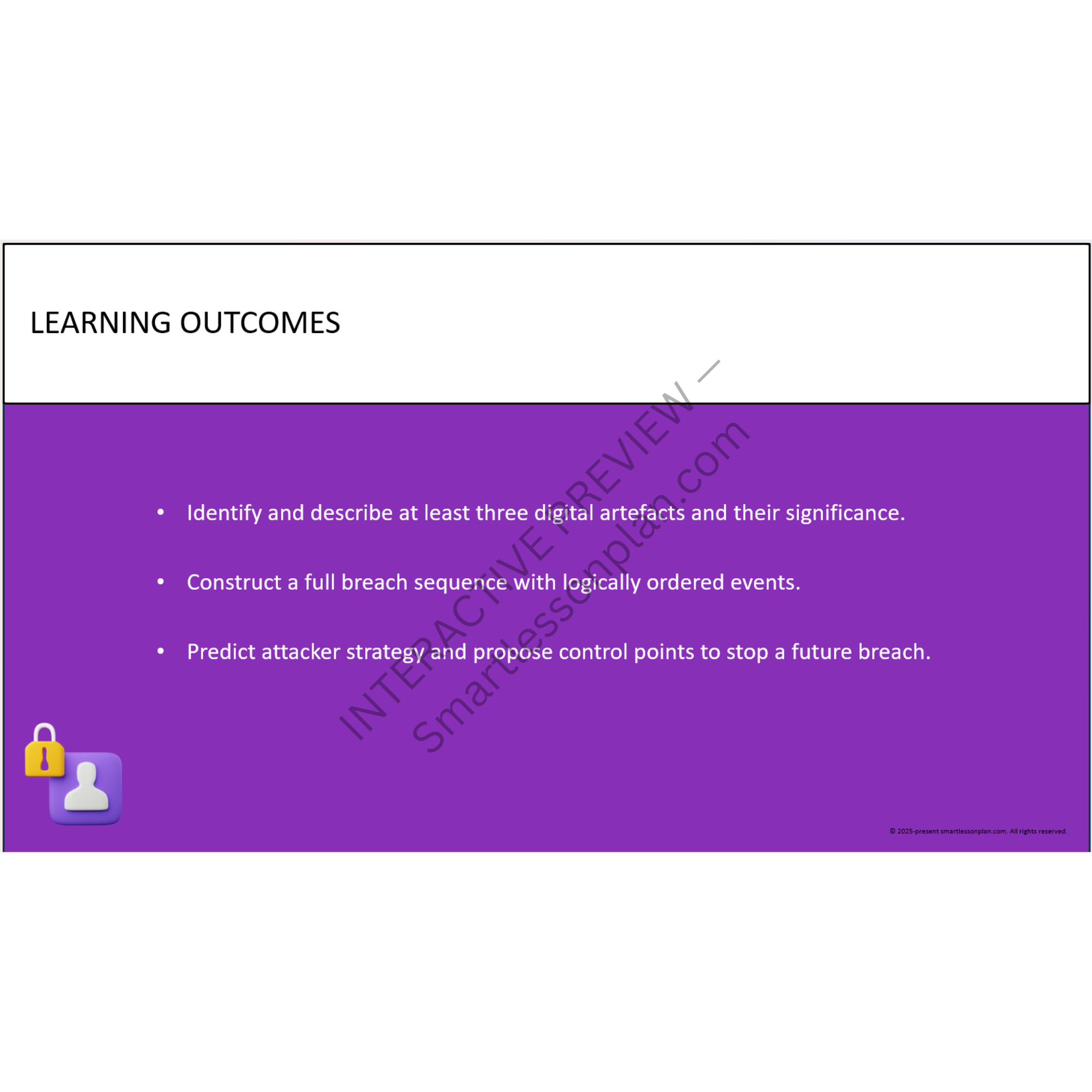
Through this, students uncover:
• How digital artefacts like login logs, alerts, and file access records reveal the breach path
• Why time correlation and trigger points are key to forensic reconstruction
• The role of audit trails, false positives, and system logic in securing modern networks
• What controls (e.g. multi-factor authentication) could have stopped the attack
Files download instantly.
Pairs well with
A next-gen lesson that keeps your curriculum aligned with emerging trends in computer science
Built for formal scrutiny — structured around intent, implementation, and impact
Includes a full inspection-grade lesson plan
Packed with high-standard classroom activities — expertly designed and immediately classroom-ready
Includes full slide-by-slide speaker notes to support confident and consistent delivery
Keeps your curriculum sharp and future-facing — with topics that reflect today’s most relevant computing advances

DF3: Lesson 1: Reconstructing a Live Cyber Attack
If you have any questions, you are always welcome to contact us. We'll get back to you as soon as possible, within 24 hours on weekdays.
-
Shipping Information
Use this text to answer questions in as much detail as possible for your customers.
-
Customer Support
Use this text to answer questions in as much detail as possible for your customers.
-
FAQ’s
Use this text to answer questions in as much detail as possible for your customers.
-
Contact Us
Use this text to answer questions in as much detail as possible for your customers.
Whats included:
Your digital download for this lesson contains 5 professionally organised folders, each containing matched teaching materials, student tasks, model answers, and full adaptations.
The lesson can be taught directly from the fully scripted presentation for confident, inspection-ready delivery.
Teacher
Resources
Support
Cover / Independent work
Classroom Adaption Guide

